Blog
Insider Threat: Your Biggest Cyber Risk Might Already Have a Company Badge
Why Identity-Centric Data Governance Is the New Frontier of Cybersecurity

Introduction: Understanding the Insider Threat
When people think of cybersecurity threats, they imagine external attackers — hackers breaching firewalls, phishing campaigns, or ransomware gangs. But many of the most damaging and costly incidents actually come from within.
An insider threat refers to any risk to an organization’s data, systems, or operations that originates from someone with legitimate access — such as an employee, contractor, or business partner. Because insiders already have credentials and a degree of trust, their actions can bypass many traditional security controls.
According to the Cybersecurity and Infrastructure Security Agency (CISA), insider incidents — whether malicious or accidental — cost organizations an average of $16.2 million per year (2024 data). That’s a staggering figure — and it underscores why insider threats are so difficult to manage.
Types of Insider Threats
Understanding the different forms of insider risk helps you design more targeted defenses. Broadly, insider threats fall into three main categories:
1. Malicious Insiders
These are individuals who intentionally abuse their access for personal, financial, or ideological reasons. Examples:
- Stealing intellectual property before leaving for a competitor.
- Selling confidential data to outsiders.
- Deliberately sabotaging systems or deleting data.
Motivations often include financial gain, revenge, coercion, or ideology.
2. Negligent Insiders
Not all damage is malicious — sometimes it’s caused by mistakes or carelessness. Examples:
- Accidentally emailing sensitive data to the wrong person.
- Using weak passwords or sharing credentials.
- Misconfiguring cloud storage (e.g., leaving an S3 bucket public).
Negligence remains one of the most common causes of insider incidents.
3. Compromised Insiders
In these cases, the insider’s credentials are hijacked by an external attacker. Examples:
- A phishing attack steals an employee’s credentials.
- A third-party vendor’s account is compromised.
Even though the intent isn’t internal, the access vector is — making this a particularly dangerous hybrid threat. These scenarios highlight why access governance is critical: a single compromised identity can expose vast amounts of data.

Figure 1: Three Common Types of Insider Threats
Why Insider Threats Are So Hard to Stop
Insiders already have:
- Valid credentials
- System knowledge
- Authorized access to sensitive data
That makes insider misuse extremely difficult to detect and prevent. Traditional defenses — firewalls, intrusion detection, endpoint protection — are designed to keep outsiders out, not insiders honest.
To manage insider risk, you need both behavioral awareness and identity control — two sides of the same coin.
Building an Insider Threat Mitigation Program
CISA’s Insider Threat 101 fact sheet outlines a practical roadmap for organizations to build or mature their insider threat programs. Key recommendations include:
- Leadership Support – Start small, define the purpose, and identify what the organization truly values.
- Reporting Culture – Create a culture of shared responsibility and provide confidential reporting pathways.
- Training and Awareness – Teach employees to recognize warning signs and concerning behaviors.
- Incident Response Planning – Ensure consistent, cross-functional response playbooks are in place.
The message is clear: insider threat mitigation should start from a cultural, organizational change.
Identity-Centric Data Governance: The Technical Foundation
While culture and awareness address the human side of insider threats, the technical defense starts with identity-centric data governance — knowing exactly who has access to what and enforcing least privilege.
Key Practices
- Unify Access Visibility: Build an inventory of all data assets and access entitlements.
- Least Privilege: Ensure users have only the data access they need to perform their role.
- Fine-Grained Controls: Apply dynamic access policies — e.g., limit data access by department, region, sensitivity level and identity behaviors (for example, if an identity hasn't accesses a sensitive data for the past 30 days, the access should be reviewed and potentially revoked).
- Continuous Review & Revocation: Automate entitlement reviews and remove unused permissions.
- Anomaly Detection: Integrate user and entity behavioral analytics (UEBA) to flag unusual access activity.
Identity-centric governance makes the Zero Trust principle actionable:
“Never trust, always verify — and limit access to the minimum necessary.”
It doesn’t eliminate insider risk entirely — but it shrinks the blast radius when incidents occur.
How CyberDesk Helps You Minimize Insider Threats
CyberDesk gives you a single pane of glass to see who has access to what, enforce least privilege, and detect risky behavior before it becomes a breach.
Here’s how:
1. Map Data to Identities
CyberDesk auto-classifies sensitive data (e.g. customer records, transaction data) and maps access down to every user and system identity — internal or third-party.
Example: Instantly spot that a third-party vendor still has access to your payments engine months after a project ended — and revoke it before it becomes a risk.
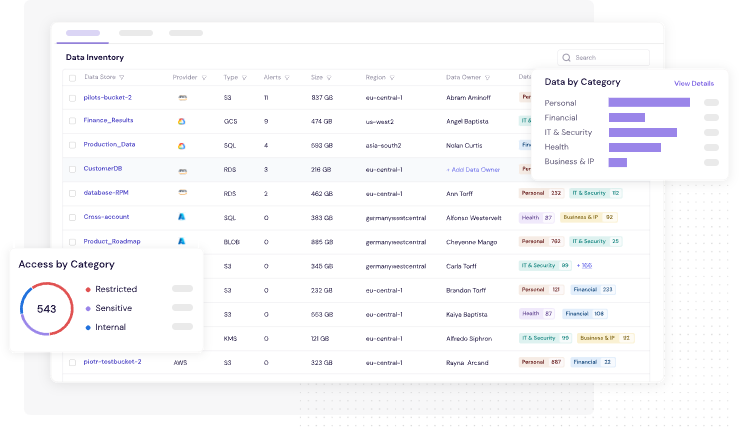
Figure 2: CyberDesk's Classification Engine Categorizes Your Organizations Data & Identities Based on Data Types and Sensitivity Levels
2. Access Graph Brings Real-Time Risk Visibility
CyberDesk’s Access Graph provides a live, visual map of how users and apps interact with sensitive data. It helps identify hidden admin paths, toxic permission combinations, and legacy access risks.
Example: Detect that a long-departed contractor still holds API-level access to your production backup bucket — and automatically flag or quarantine it.
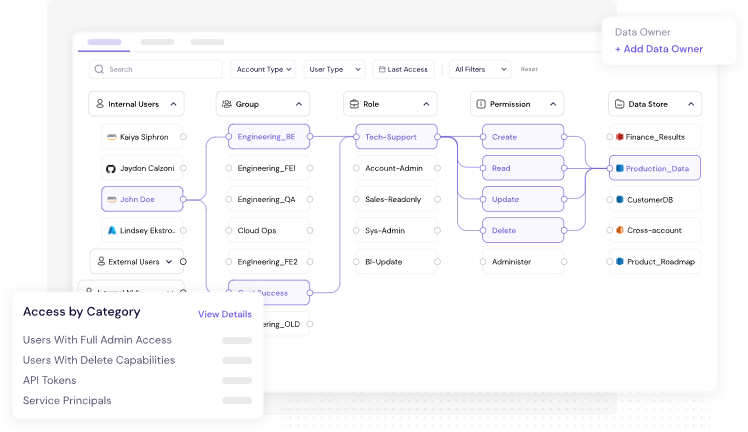
Figure 3: CyberDesk's Access Graph Provides Identity & Data Level Visibility
3. Prevent Over-Permissioning
Set and monitor for least privilege. With automated alerts when access exceeds policy. You can block high-risk access in real time or flag it for review.
Example: A junior analyst suddenly gains write access to regulatory filing databases? CyberDesk flags it immediately, stops the escalation, and alerts compliance teams.
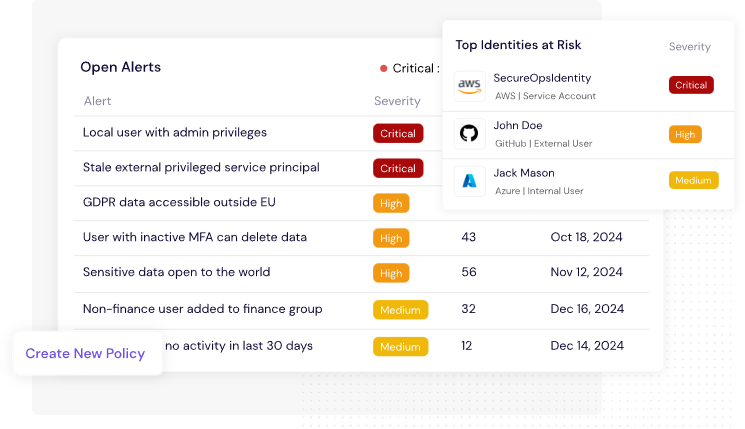
Figure 4: CyberDesk's Alerts Dashboard Facilitates Breach Risk Mitigation
4. Automated Access Reviews
Run periodic or ad hoc access reviews with full audit trails. Managers get intelligent prompts, and reviews are stored securely for inspection.
Example: Automatically trigger a 30-day review cycle for all admin-level cloud accounts. Managers receive guided prompts to approve, modify, or revoke access — all logged for audit.
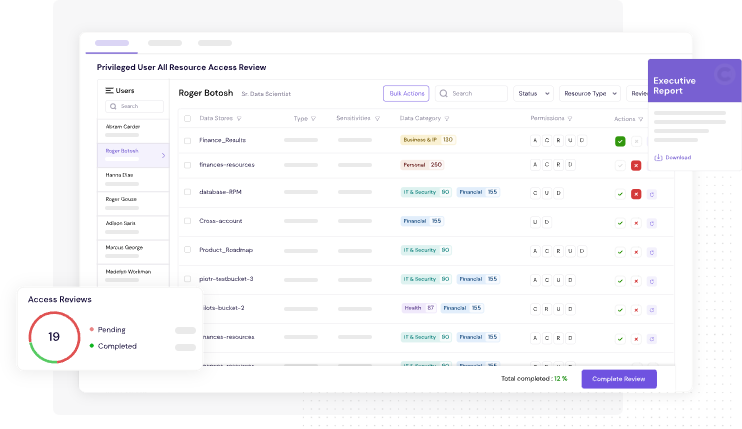
Figure 5: CyberDesk's Access Review Frees You Up From Time-Consuming Manual Processes and Helps You Stay Compliant
Want to See CyberDesk in Action?
Learn how CyberDesk can help you to adaptively control who can take what actions on what data.
Founders
Dr. Tobias Lieberum & Prabhakar Mishra
Year of foundation
2022
Headquarters
Munich, Germany
About CyberDesk
Founded in 2022 and based in Munich, Germany, CyberDesk is led by Dr. Tobias Lieberum and Prabhakar Mishra. In their previous careers in sensitive environments in banking and consulting, the founders firsthand witnessed the challenges of securing data access in the cloud. In lack of a satisfactory solution, they decided to solve this global threat themselves.
For media inquiries, please contact the CyberDesk communications team
We will be happy to connect with you. Contact CyberDesk today.
Partners
Copyright © CyberDesk GmbH 2026. All rights reserved.

