Blog
The Rise of Identity Visibility and Intelligence Platforms (IVIP)
Why Identity Visibility Is the New Foundation of Data Security

With identity-related incidents accounting for 70% of breaches (RSA), identity has long become the new security perimeter — but visibility remains its weakest point. Despite major investments in IAM, PAM, and CIEM, many organizations still struggle to answer a deceptively simple question: Who has access to what data?
In 2025, Gartner officially recognized Identity Visibility and Intelligence Platforms (IVIP) as a new category on the Hype Cycle for Digital Identity. The timing is no coincidence. As enterprises expand across multi-cloud environments and adopt AI-driven automation, the complexity of managing both human and machine identities has reached a breaking point.
This article explores what IVIP means, why it matters now, and how it redefines identity-centric data security for the AI era.
From Fragmented Identity Stacks to Unified Visibility
Over the past decade, enterprise identity architecture has evolved into a patchwork of specialized tools.
- Identity Providers (IDPs) manage authentication and single sign-on.
- IGA solutions govern user lifecycles and certifications.
- PAM platforms secure privileged accounts.
- CIEM and secrets management tools protect cloud and API credentials.
Each tool serves a purpose — but each also creates a new silo of identity data. The result: dozens of disconnected systems, each aware of its own entitlements but blind to the rest.
When a CISO asks, “Who can access our customer database?” the answer may span Active Directory, Azure, AWS, Google Drive, and hundreds of SaaS apps. Without correlation, teams spend days reconciling exports and permissions spreadsheets. In a world of continuous change, that’s already too late.
Fragmentation isn’t just inconvenient; it’s a risk amplifier. Without visibility across identity systems, organizations can’t enforce least privilege, prove compliance, or respond quickly to incidents.
Visibility is no longer a luxury — it’s the foundation of digital trust.
What Is an Identity Visibility and Intelligence Platform (IVIP)?
An Identity Visibility and Intelligence Platform is the intelligence layer that unifies identity data across your environment. It doesn’t replace IAM; it connects and explains it.
In essence, an IVIP:
- Collects identity, account, and entitlement data from multiple sources — IDPs, IGAs, PAMs, HR systems, SaaS apps, and data platforms.
- Correlates these data points into a single model linking people, service accounts, roles, and effective permissions.
- Analyzes for risk: orphaned entitlements, toxic combinations, dormant privileges, or policy drift.
- Visualizes the entire “who-can-do-what” map — across clouds, apps, and data stores.
- Generates audit-ready evidence to prove compliance with DORA, NIS2, and other frameworks.
Think of IVIP as the connective tissue between your existing identity systems — turning static configuration data into actionable intelligence.
Traditional IAM systems manage processes. IVIP provides context. It tells you not just who has access, but what that access actually means.
Why IVIP Matters Now
1. The Identity Explosion
Today, non-human identities — service accounts, API keys, workloads, AI agents — outnumber employees in many enterprises by dozens to one. Each carries entitlements, tokens, and credentials that can expose sensitive data if misconfigured. IVIP delivers the unified visibility required to govern this new, machine-driven identity landscape.
2. Regulatory Pressure in Europe
Regulations such as the Digital Operational Resilience Act (DORA) and NIS2 Directive now demand continuous monitoring of access relationships and provable control over data exposure. Manual certifications and quarterly reviews no longer suffice. IVIP platforms automate this visibility, producing contextual evidence for regulators and auditors in real time.
3. Zero Trust at Scale
“Never trust, always verify” is impossible if you can’t see what identities exist or what they can access. IVIP provides the necessary visibility layer to enforce least-privilege principles and validate that policies behave as intended across environments.
4. Operational Efficiency
Security and compliance teams waste countless hours cross-referencing IAM exports and cloud configurations. IVIP reduces that effort dramatically by centralizing identity intelligence, cutting investigation time, and enabling faster remediation.
5. AI Readiness
AI and automation amplify identity sprawl. Every new model, agent, or API integration creates fresh service credentials and tokens. IVIP ensures organizations can track and govern these fast-moving identities before they become blind spots in data security.
How IVIP Complements the IAM Stack
The existing IAM stack already includes robust components:
- IDP → controls authentication and access policies.
- IGA → manages identity lifecycle and recertifications.
- PAM → secures privileged access.
But none of them provides continuous, contextual insight into effective permissions across systems.
That’s where IVIP adds value:
- Verification: Confirms IAM policies behave as intended in real environments.
- Correlation: Connects user accounts, service identities, and entitlements across sources.
- Context: Explains why certain access exists — and whether it still makes sense.
- Evidence: Delivers clean, defensible audit artifacts on demand.
If IAM is the nervous system of digital identity, IVIP is its sense of sight — revealing the connections that make risk and compliance visible.
Real-World IVIP Use Cases
1. Access Drift Detection IVIP continuously compares current access rights to approved policies, flagging when entitlements expand unintentionally.
2. Joiner–Mover–Leaver Validation When employees change roles or depart, IVIP verifies that all associated accounts, tokens, and keys are updated or revoked across systems.
3. Privileged Access Hygiene The platform identifies dormant admin accounts, bypass paths, and toxic combinations before attackers do.
4. M&A Integration Following mergers or divestitures, IVIP maps entitlements across tenants to expose redundant or risky overlaps instantly.
5. Audit Automation Instead of exporting data manually for auditors, IVIP generates complete, contextual evidence packs — reducing weeks of work to hours.
The outcome: Fewer blind spots, faster audits, and decisions backed by clear, defensible visibility.
The Future: IVIP and Context-Aware Security in the AI Era
As enterprises adopt generative AI, the number of identities and security complexity will multiply exponentially. Managing them manually will become impossible. IVIP represents the bridge between human oversight and AI automation in identity security.
Tomorrow’s IVIPs will:
- Leverage machine learning to predict risky privilege escalations.
- Use behavioral baselines to detect abnormal access patterns.
- Employ natural-language reasoning to explain identity risk to auditors and executives.
- Integrate with ITDR and ISPM systems to support automated remediation.
The goal is not just to see, but to understand — and eventually, to act. Visibility and intelligence form the foundation for the next phase of identity automation.
CyberDesk: Bringing Identity Intelligence to Life
CyberDesk exemplifies the core vision behind Identity Visibility and Intelligence Platforms (IVIP). It unifies identity and data intelligence into a single, adaptive layer that answers the most fundamental question in security: who can access what data, and why?
And here’s how we do it:
1. Map Data to Identities
CyberDesk auto-classifies sensitive data (e.g. customer records, transaction data) and maps access down to every user and system identity — internal or third-party.
Example: Instantly spot that a third-party vendor still has access to your payments engine months after a project ended — and revoke it before it becomes a risk.
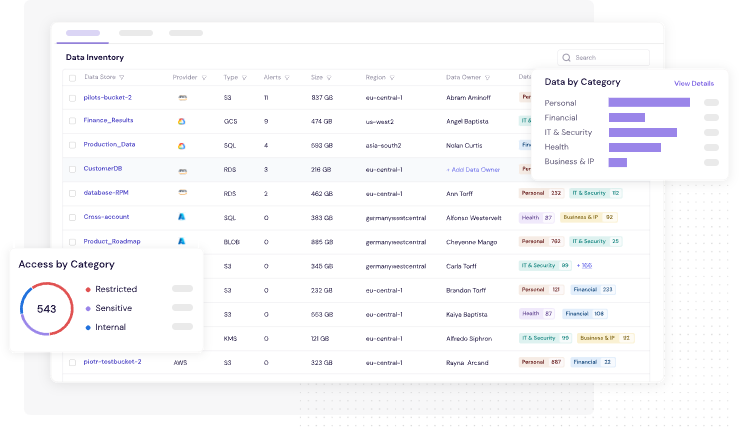
Figure 1: CyberDesk's Classification Engine Categorizes Your Organizations Data & Identities Based on Data Types and Sensitivity Levels
2. Access Graph Brings Real-Time Risk Visibility
CyberDesk’s Access Graph provides a live, visual map of how users and apps interact with sensitive data. It helps identify hidden admin paths, toxic permission combinations, and legacy access risks.
Example: Detect that a long-departed contractor still holds API-level access to your production backup bucket — and automatically flag or quarantine it.
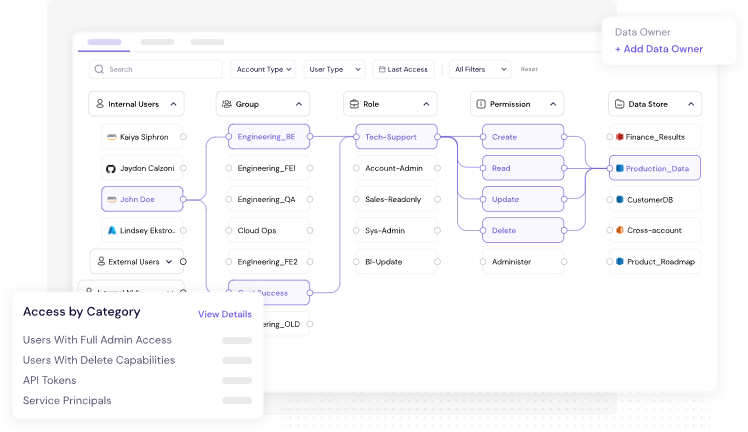
Figure 2: CyberDesk's Access Graph Provides Identity & Data Level Visibility
3. Prevent Over-Permissioning
Set and monitor for least privilege. With automated alerts when access exceeds policy. You can block high-risk access in real time or flag it for review.
Example: A junior analyst suddenly gains write access to regulatory filing databases? CyberDesk flags it immediately, stops the escalation, and alerts compliance teams.
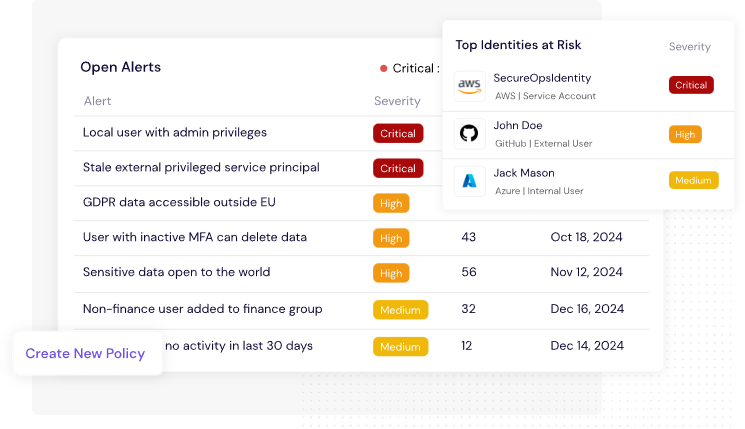
Figure 3: CyberDesk's Alerts Dashboard Facilitates Breach Risk Mitigation
4. Automated Access Reviews
Run periodic or ad hoc access reviews with full audit trails. Managers get intelligent prompts, and reviews are stored securely for inspection.
Example: Automatically trigger a 30-day review cycle for all admin-level cloud accounts. Managers receive guided prompts to approve, modify, or revoke access — all logged for audit.
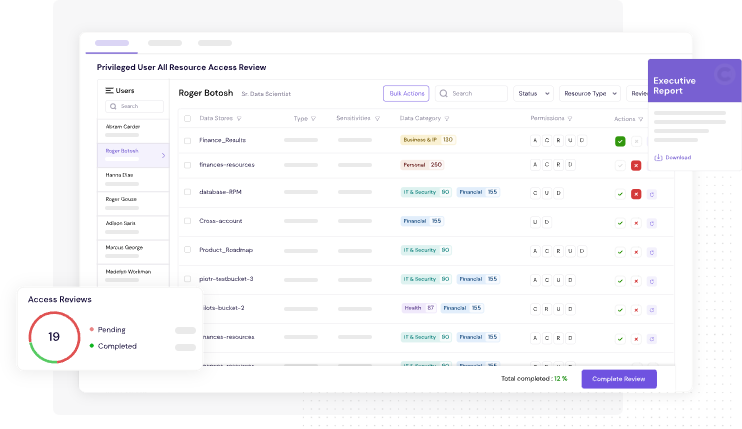
Figure 4: CyberDesk's Access Review Frees You Up From Time-Consuming Manual Processes and Helps You Stay Compliant
Want to See CyberDesk in Action?
Learn how CyberDesk can help you to adaptively control who can take what actions on what data.
Founders
Dr. Tobias Lieberum & Prabhakar Mishra
Year of foundation
2022
Headquarters
Munich, Germany
About CyberDesk
Founded in 2022 and based in Munich, Germany, CyberDesk is led by Dr. Tobias Lieberum and Prabhakar Mishra. In their previous careers in sensitive environments in banking and consulting, the founders firsthand witnessed the challenges of securing data access in the cloud. In lack of a satisfactory solution, they decided to solve this global threat themselves.
For media inquiries, please contact the CyberDesk communications team
We will be happy to connect with you. Contact CyberDesk today.
Partners
Copyright © CyberDesk GmbH 2026. All rights reserved.

