CISO's Playbook
Safely Deploying Microsoft Copilot
Driving Innovation Without Losing Control of Your Data

Introducing Microsoft Copilot into enterprise environments can unlock significant productivity potential by leveraging AI to support users across Microsoft 365 services. However, with great power comes great responsibility. According to Gartner, 40% Copilot rollouts are delayed due to data security roadblocks. For Chief Information Security Officers and IT leaders responsible for enterprise data security, it is critical to ensure that Copilot's capabilities align with organizational security and compliance requirements. This whitepaper outlines the key considerations and best practices for securely deploying and operating Microsoft Copilot, emphasizing data access, governance, and risk mitigation strategies.
Understanding How Microsoft Copilot Works and Its Data Security Risks
To appreciate the data security challenges posed by Microsoft Copilot, it’s essential to understand how it works. Copilot integrates seamlessly into Microsoft 365 applications, such as Word, Excel, Outlook, and Teams, acting as a virtual assistant that automates tasks, analyzes data, and generates outputs tailored to user needs. While its capabilities are transformative, Copilot’s operation introduces significant data security risks that every organization must address.
How Microsoft Copilot Works
Microsoft Copilot relies on deep integration with your Microsoft 365 environment, accessing data from multiple sources to generate relevant insights and outputs. Here's how it functions:
- User Contextual Input:Users provide a prompt or task, such as drafting a report, analyzing a spreadsheet, or summarizing a meeting.
- Data Aggregation:Copilot pulls data from Microsoft 365 applications, including files, emails, chat histories, and shared drives, to craft its response.
- Large Language Model (LLM) Processing:Copilot sends the user input to its underlying AI model, which interprets the prompt, processes the data, and generates a tailored response or action.
- Output Delivery:The AI-generated output is delivered directly to the user, often blending data from various organizational sources.
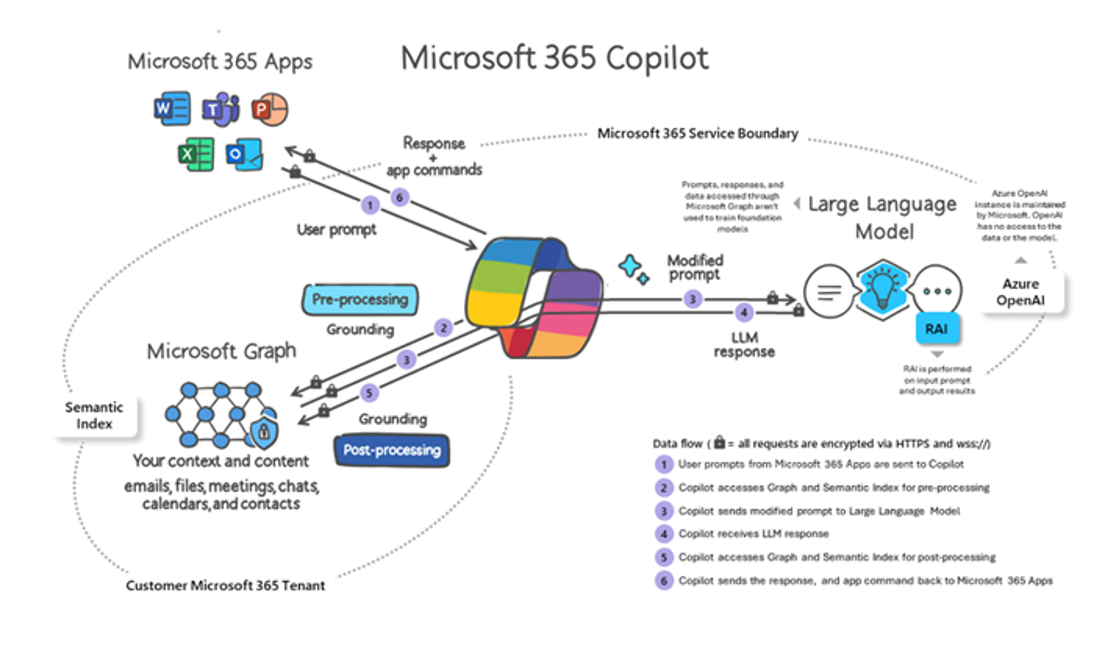
Figure 1: Illustration of Working Mechanism of Microsoft Copilot
So Where Do the Risks Lie?
It is worth mentioning that Microsoft Copilot operates using the access permissions of the logged-in user. This fundamental design ensures that Copilot respects existing organizational access controls and permissions. However, that’s exactly where the risk lies. Because Copilot inherits a user’s permissions, if the user has access to sensitive data—whether relevant to their current task or not—Copilot may still surface that information into its output, potentially leading to unintended data exposure or a security breach.
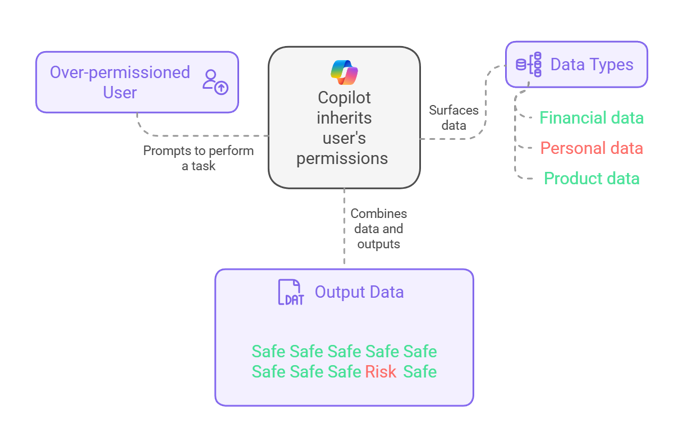
Figure 2: Illustration of An Over-permissioned User Performing Tasks With Copilot
“>95% of standing access rights are not used” -- Microsoft State of Cloud Permissions Risks Report 2023
Best Practices of Mitigating Data Security Risks
Organizations must ensure that users have only the permissions they need to perform their roles effectively. By enforcing the principle of least privilege and regularly auditing permissions, organizations can significantly mitigate the risks associated with Microsoft Copilot’s implementation.
Here are some best practices when rolling out and operating Microsoft Copilot:
1. Regularly Review and Update User Permissions:
Conducting periodic audits of user permissions is essential to ensure they align with roles and responsibilities. Tools that automate access reviews and provide detailed insights into risky identities can greatly enhance this process, enabling organizations to mitigate over-permissioning risks and adhere to the principle of least privilege.
A clear visualization of access entitlements is also invaluable for managing permissions. Mapping how user roles connect to data resources helps identify excessive permissions, offering actionable insights to refine access controls. Tools like Access Graph, for example, help organizations visualize via which groups, roles, and permissions their identities – whether human or nun-human – can access sensitive data.
2. Implement Data Classification and Sensitivity Labeling:
Establishing and enforcing data classification policies is a foundational step in protecting sensitive information. Automatic classification tools e.g. Microsoft Purview can standardize the labeling process, ensuring consistency and reducing human error. These tools can also extend sensitivity labeling to platforms like SharePoint and OneDrive, enhancing the protection of stored data.
Ideally, not only should data be classified, but identities should also be classified and consolidated into a holistic view. At CyberDesk, this is achieved through Data Inventory and Identity Inventory tools, which streamline these processes effectively and provide organizations the highest level of visibility with an intuitive visual mapping system.
3. Implement Access Controls and Activity Monitoring:
Conditional access policies and activity monitoring are essential for securing high-risk operations. Effective solutions should enable detailed logging and anomaly detection, helping teams pinpoint unusual patterns of behavior. To maximize effectiveness, organizations should ensure proper configuration of governance rules and establish contextual monitoring systems to oversee identity and data interactions. Real-time monitoring can help promptly identify and address anomalies or misconfigurations, reducing the risk of potential data breaches or compliance issues.
4. Educate and Train Users:
A strong security posture relies on user awareness and adherence to best practices. Training programs should emphasize the risks of sharing sensitive information and guide users on proper data handling. Nevertheless, by embedding automated safeguards that reduce user error, organizations can create a culture of compliance without burdening employees.
The Role of CyberDesk in Securing Microsoft Copilot
CyberDesk has a proven methodology for securing data during Microsoft Copilot rollouts, leveraging a structured approach to eliminate unused access, enhance transparency, and ensure compliance. By focusing on key aspects such as data sensitivity, access management, and policy redesign, CyberDesk provides organizations with a reliable framework to safeguard their environments and enable a seamless Copilot implementation.
CyberDesk addresses these challenges through a sequential five-step process:
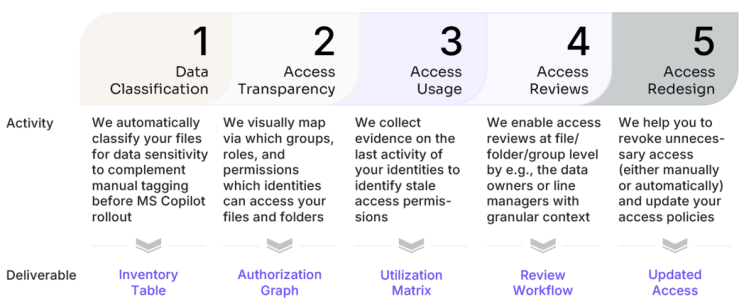
Figure 3: CyberDesk's 5-step Approach on Securing Microsoft Copilot Deployment
This comprehensive approach helps organizations adhere to the principle of least privilege, reduce risk, and foster a secure foundation for leveraging Microsoft Copilot.
Closing Remarks
Microsoft Copilot has the potential to revolutionize productivity, but its adoption must be carefully managed to safeguard enterprise data. By implementing robust access controls, adopting sensitivity labeling, leveraging advanced data security tools, organizations can mitigate risks and ensure Copilot aligns with their security and compliance objectives.
For technology leaders, the successful deployment of Copilot is not just a technical endeavor but a strategic initiative requiring a proactive approach to data security and governance. As the pioneer of identity-centric data security in the EU and recognized as a Rising Star by Kuppinger Cole, CyberDesk has successfully guided clients across various industries on their data security transformation journeys. We would love to support your organization as well.
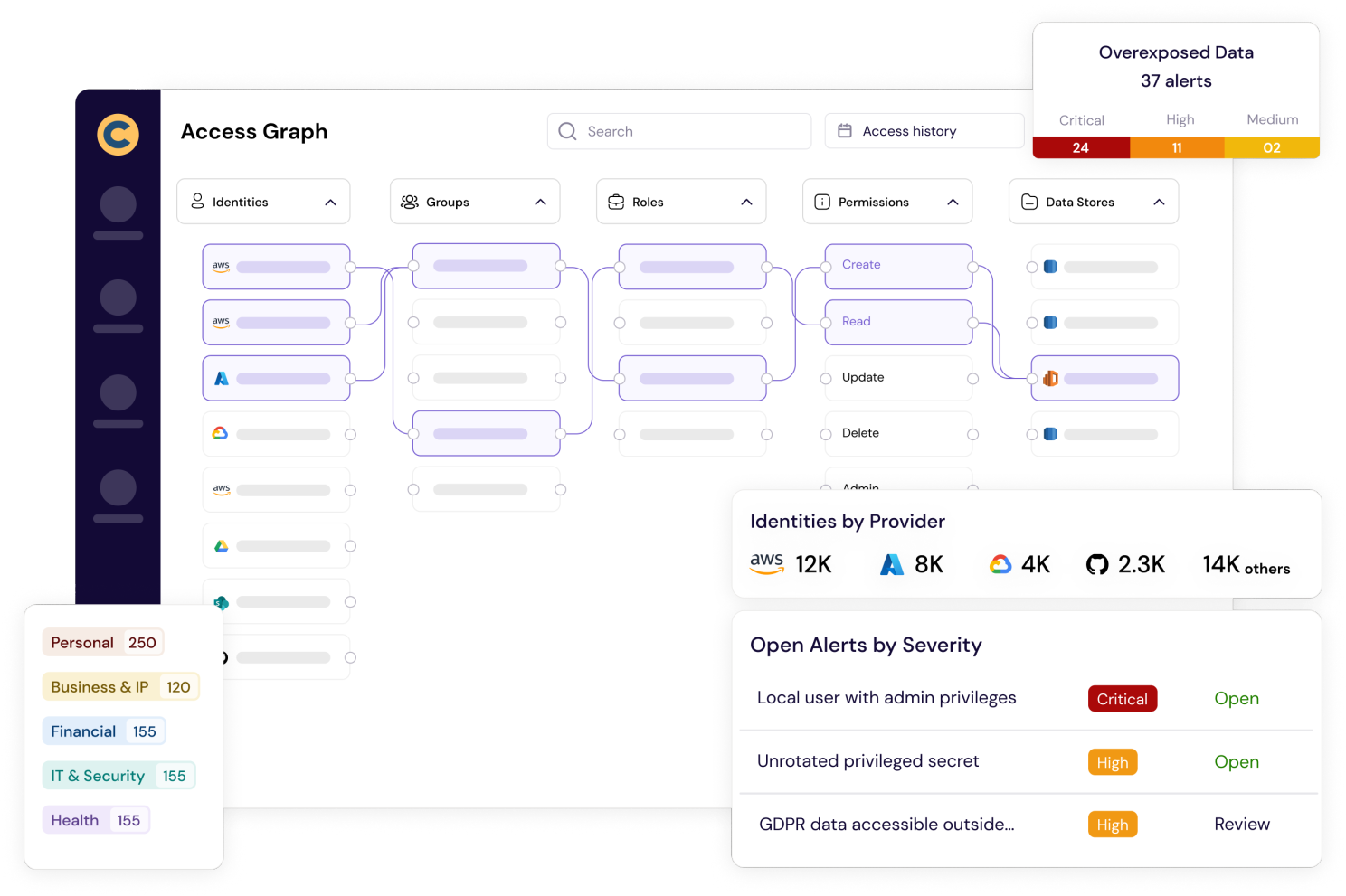
CyberDesk provides you full visibility across all your human and non-human identities
Want to See CyberDesk in Action?
Learn how CyberDesk can help secure your data when deploying Microsoft Copilot.
Founders
Dr. Tobias Lieberum & Prabhakar Mishra
Year of foundation
2022
Headquarters
Munich, Germany
About CyberDesk
Founded in 2022 and based in Munich, Germany, CyberDesk is led by Dr. Tobias Lieberum and Prabhakar Mishra. In their previous careers in sensitive environments in banking and consulting, the founders firsthand witnessed the challenges of securing data access in the cloud. In lack of a satisfactory solution, they decided to solve this global threat themselves.
For media inquiries, please contact the CyberDesk communications team
We will be happy to connect with you. Contact CyberDesk today.
Partners
Copyright © CyberDesk GmbH 2026. All rights reserved.

